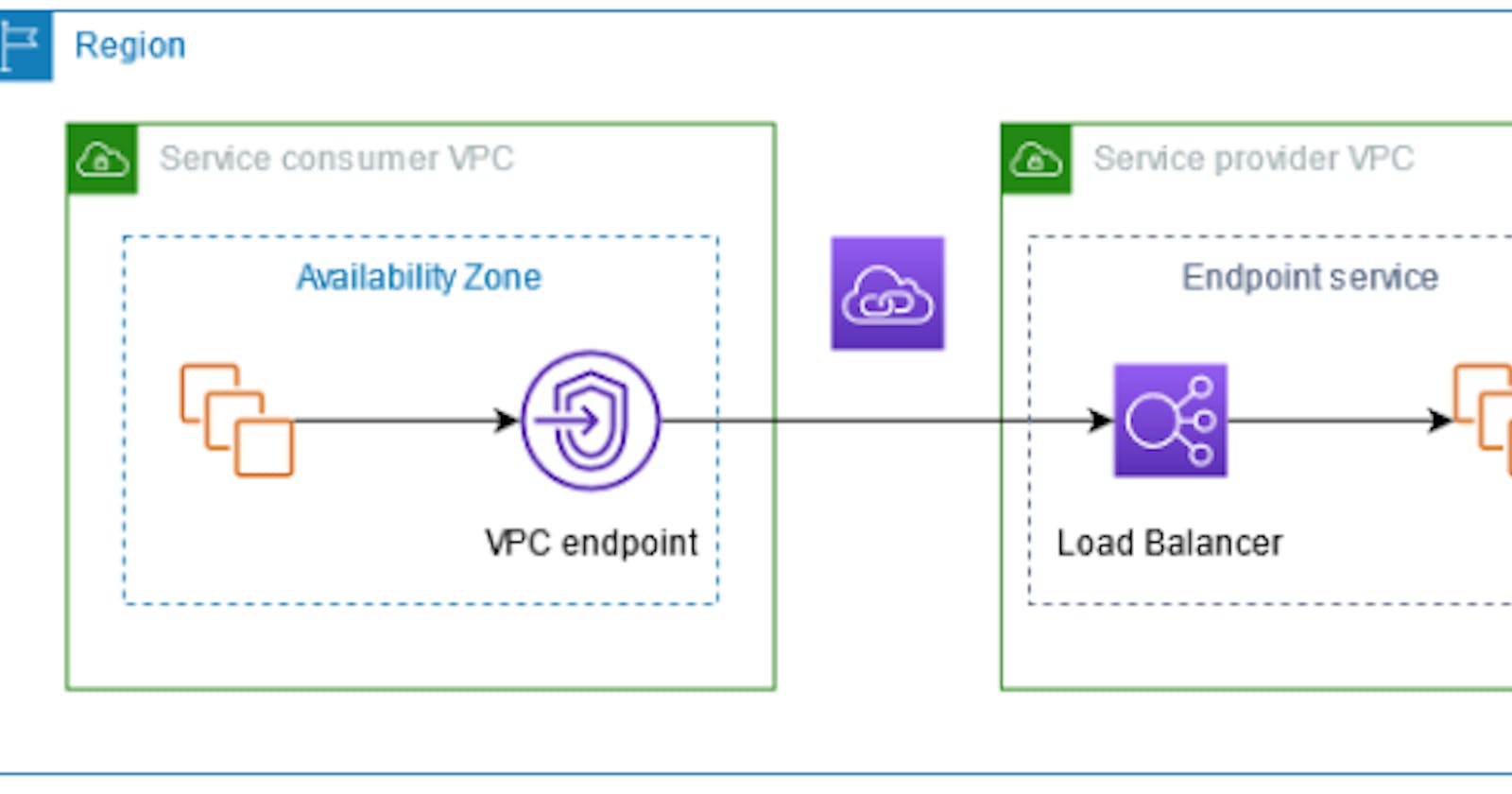
A VPC endpoint enables you to privately connect your VPC to supported AWS services and VPC endpoint services powered by PrivateLink without requiring an internet gateway, NAT device, VPN connection, or AWS Direct Connect connection. Instances in your VPC do not require public IP addresses to communicate with resources in the service. Traffic between your VPC and the other service does not leave the Amazon network.

VPC Endpoints
Service consumers create VPC endpoints to connect their VPCs to endpoint services, specifying the service name of the endpoint service during creation. There are three types of VPC endpoints:
Interface Endpoint: For TCP traffic to an endpoint service, resolved using DNS.
Gateway Load Balancer Endpoint: Routes traffic to virtual appliances via private IP addresses, distributing traffic and scaling with demand.
Gateway Endpoint: Routes traffic to Amazon S3 or DynamoDB without using AWS PrivateLink.
Endpoint Network Interfaces
Each subnet specified when creating a VPC endpoint has an associated endpoint network interface, serving as an entry point for traffic. IPv4 or IPv6 addresses are assigned based on endpoint support. IPv6 addresses are unreachable from the internet.
Endpoint Policies
VPC endpoint policies, IAM resource policies attached to VPC endpoints, control access to the endpoint service. The default policy permits all actions by all principals on all resources.
Endpoint States
VPC endpoints have various states:
PendingAcceptance: Initial state for manually accepted connection requests.
Pending: Initial state for automatically accepted requests or if modified by the consumer.
Available: Ready for use.
Rejected: Request rejection by the service provider.
Expired: Connection request expiration.
Failed: Unsuccessful availability attempt.
Deleting: Deletion in progress.
Deleted: Endpoint deletion.
AWS PrivateLink Connections
Connections between VPC endpoints and endpoint services ensure traffic stays within the AWS network, avoiding the public internet. Service providers permit access to the endpoint service, with consumers initiating and providers accepting or rejecting connections. Interface VPC endpoints offer endpoint policies for access control by IAM principals.
Steps
- Create the vpc

- Create public and private subnet

- Create Internet Gateway

- Attach Internet Gateway to the vpc

- Create public(rt1) and private(rt2) route tabble

- Attach Internet Gateway to the public route table

- Associate public and private subnet to their respective route table


- Create vpc endpoints. And add private route table and s3 services as gateway

- Create ec2 in which private ec2 is amazon linux because aws cli is by default configured so that it is easy to access aws cli in the absence of the internet access in the private sub net. If you want to use other instance like ubuntu then you need to configure NAT gateway to access internet and then aws cli. Choice is yours

- Enter into public instace and from there login into private instace

- Then finally access the S3 bucket from private ec2

Thanks for reading ....................................