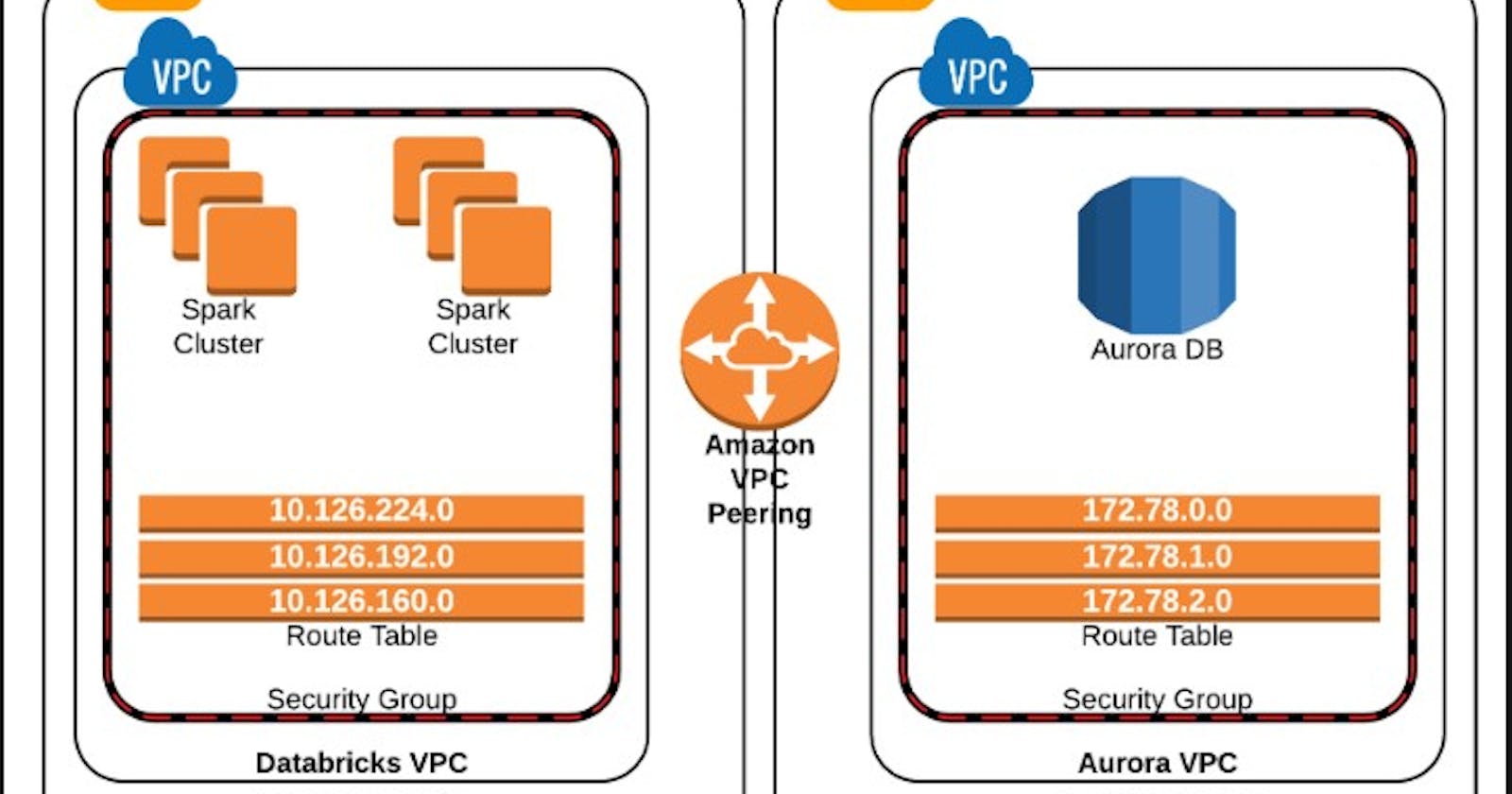
VPC (Virtual Private Cloud) peering is a networking connection between two VPCs that enables them to communicate with each other as if they were within the same network. This allows resources within each VPC to interact with resources in the other VPC securely and efficiently. Here are some important terms related to VPC peering:
VPC (Virtual Private Cloud): A virtual network in the cloud that you create within AWS. It allows you to launch AWS resources, such as EC2 instances or RDS databases, into a virtual network that you've defined.
Peering Connection: A networking connection between two VPCs that enables them to communicate with each other using private IP addresses as if they were part of the same network.
Accepter VPC: The VPC that receives the peering connection request and accepts it. Once accepted, this VPC becomes the accepter VPC for the peering connection.
Requester VPC: The VPC that initiates the peering connection request. It requests to establish a peering connection with another VPC.
Peering Connection: Once the peering connection request is accepted, a peering connection is established between the two VPCs. This connection enables the exchange of traffic between the VPCs.
Route Tables: Each VPC has associated route tables that determine how traffic is routed within the VPC. When a peering connection is established, route tables must be updated to allow traffic to be routed between the peered VPCs.
CIDR Blocks: Each VPC is associated with a CIDR (Classless Inter-Domain Routing) block, which defines the range of IP addresses that can be used within the VPC.
Security Groups: Security groups act as virtual firewalls for your EC2 instances and other resources within a VPC. They control inbound and outbound traffic based on rules that you define.

Steps
- Create two VPCi.e vpc1 and vpc2

- Create sub-net in each vpc

- Create Internet gateway for each vpc

- Attach internet gateway to each vpc

- Create two route table for each vpc

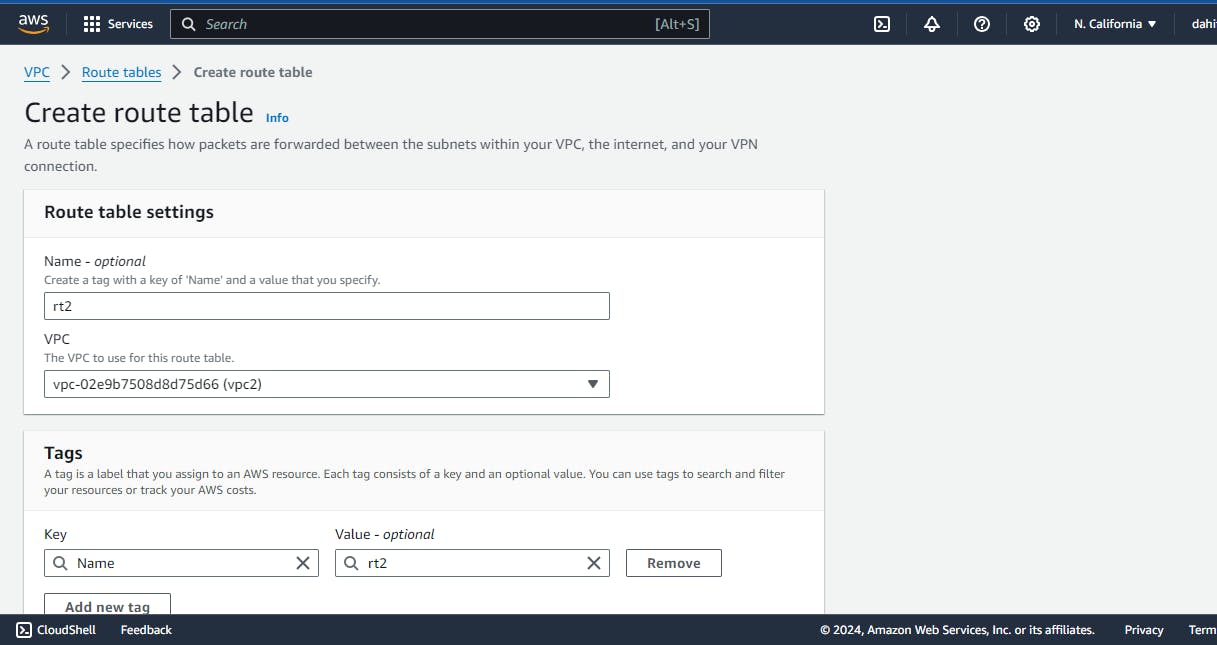
- create two ec2 in each vpc
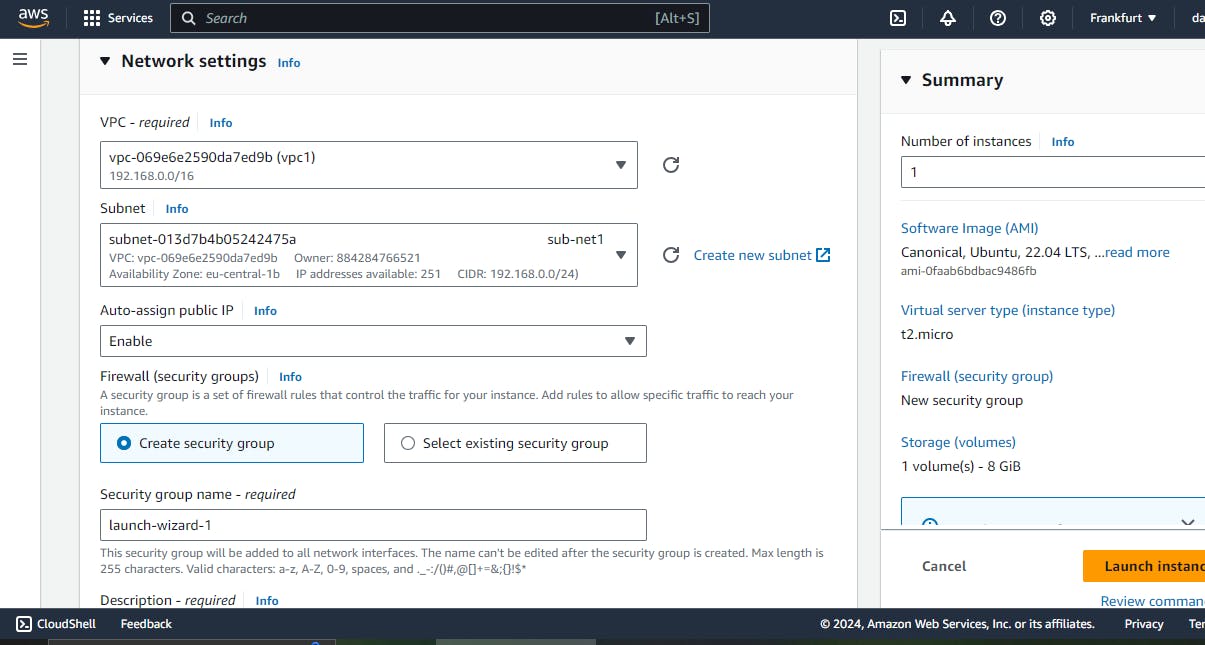
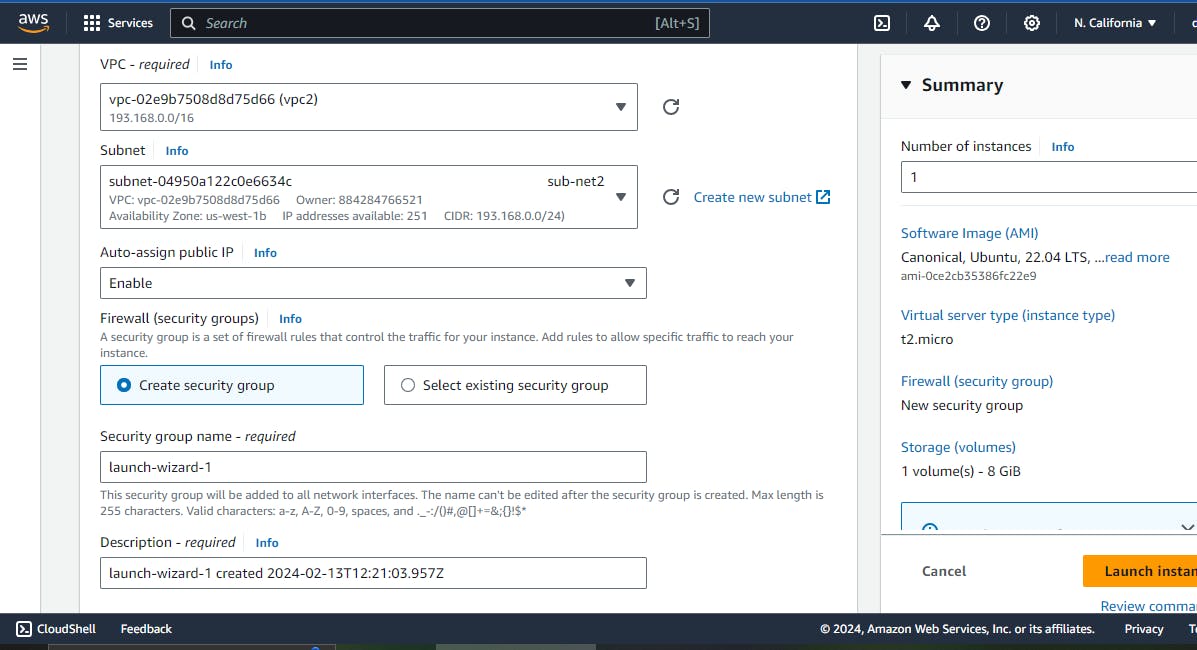
- Associate sub-net in each vpc


- Attach internet gateway to route table to access internet in the vpc
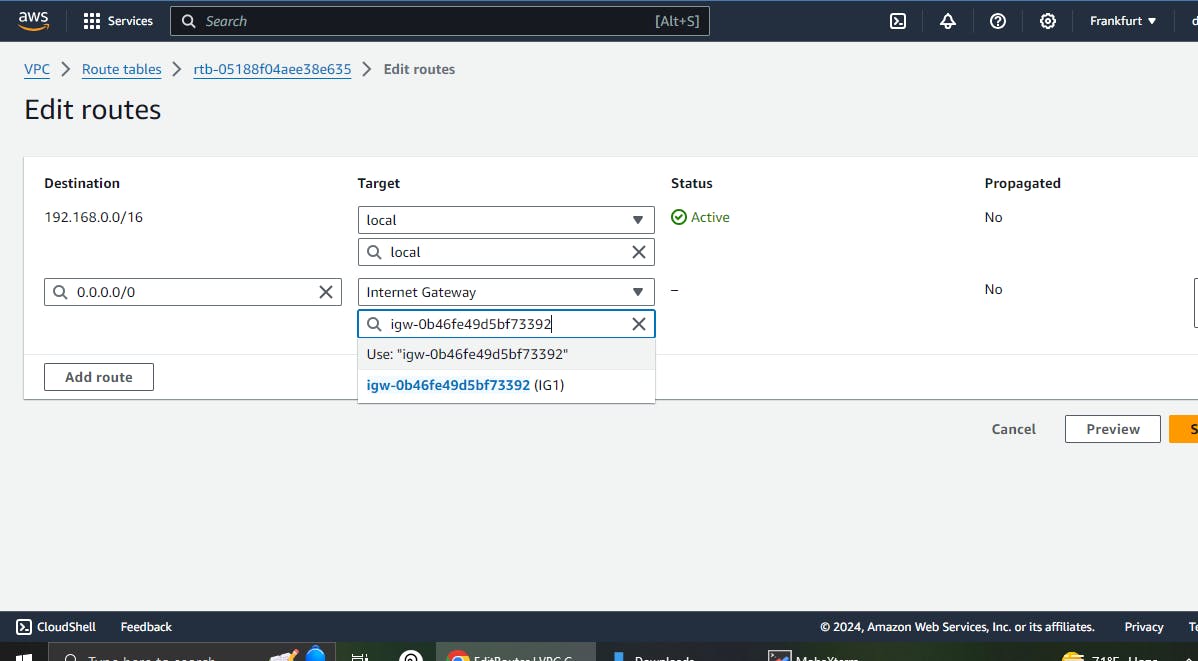
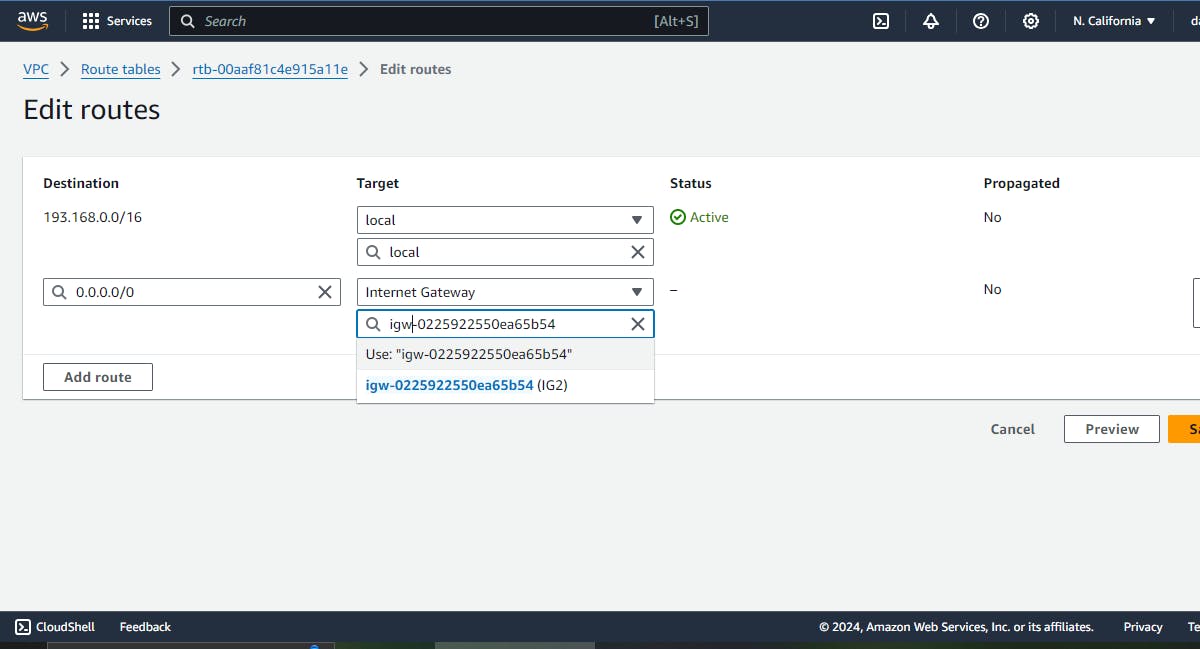
- Create vpc peering from vpc1 to vpc2 .
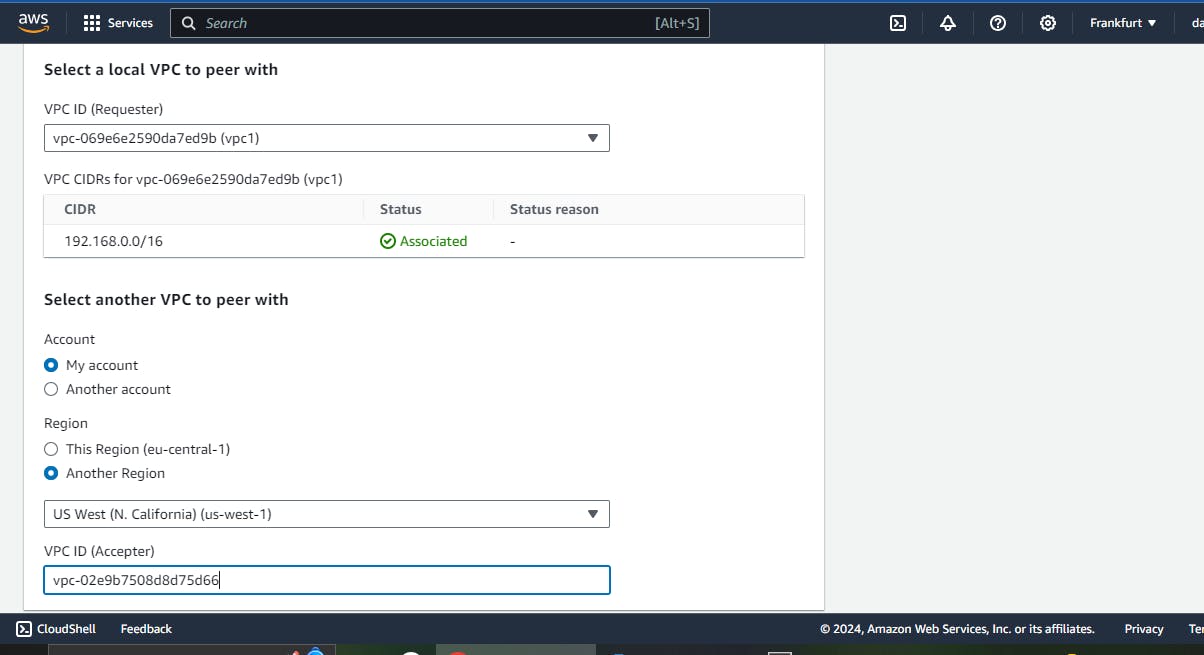
- Then accept peering request from vpc2

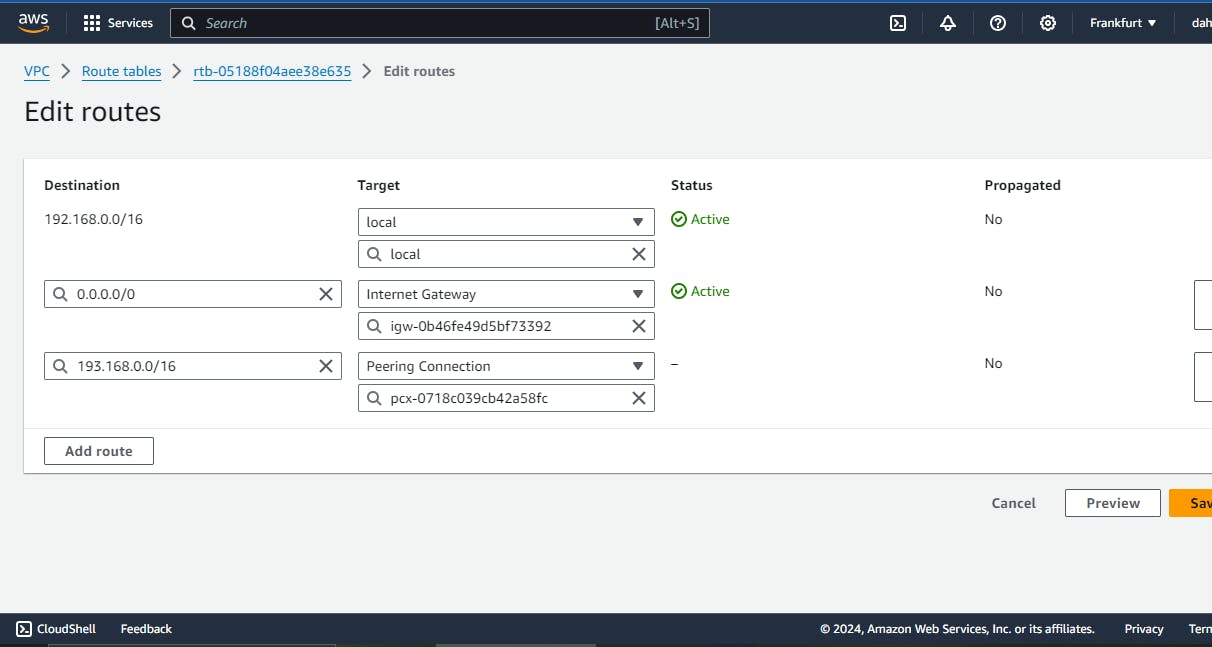
- update route table by adding the peering connetion like following
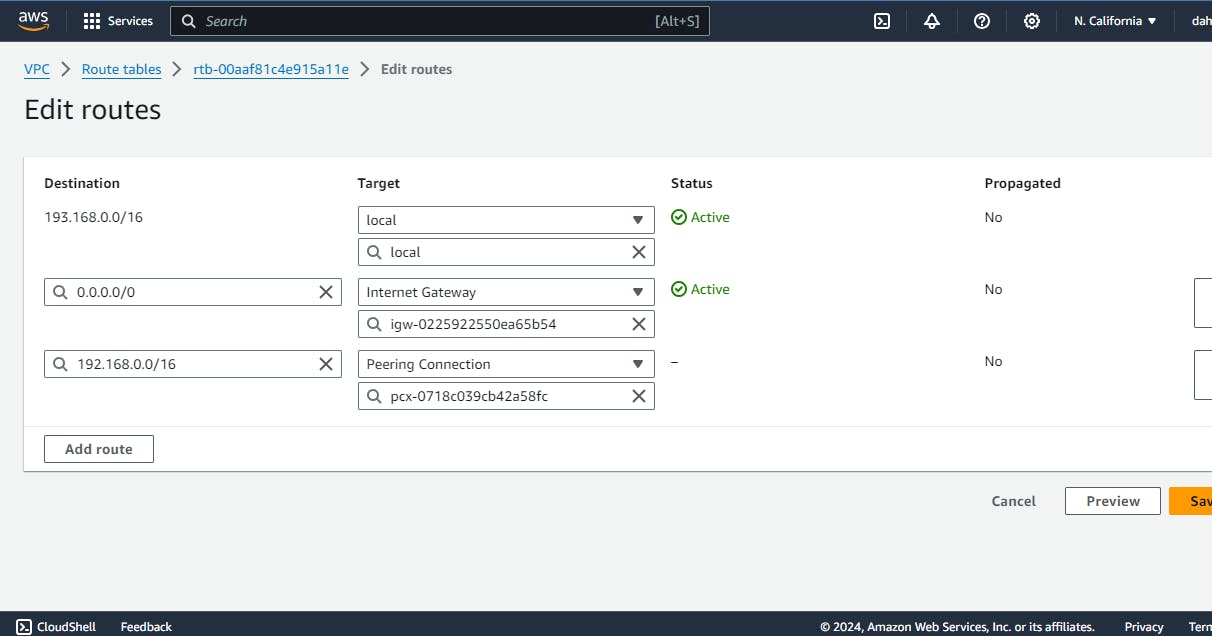
- One more thing that for an ec2 instance, make sure that the security groups inbound rule
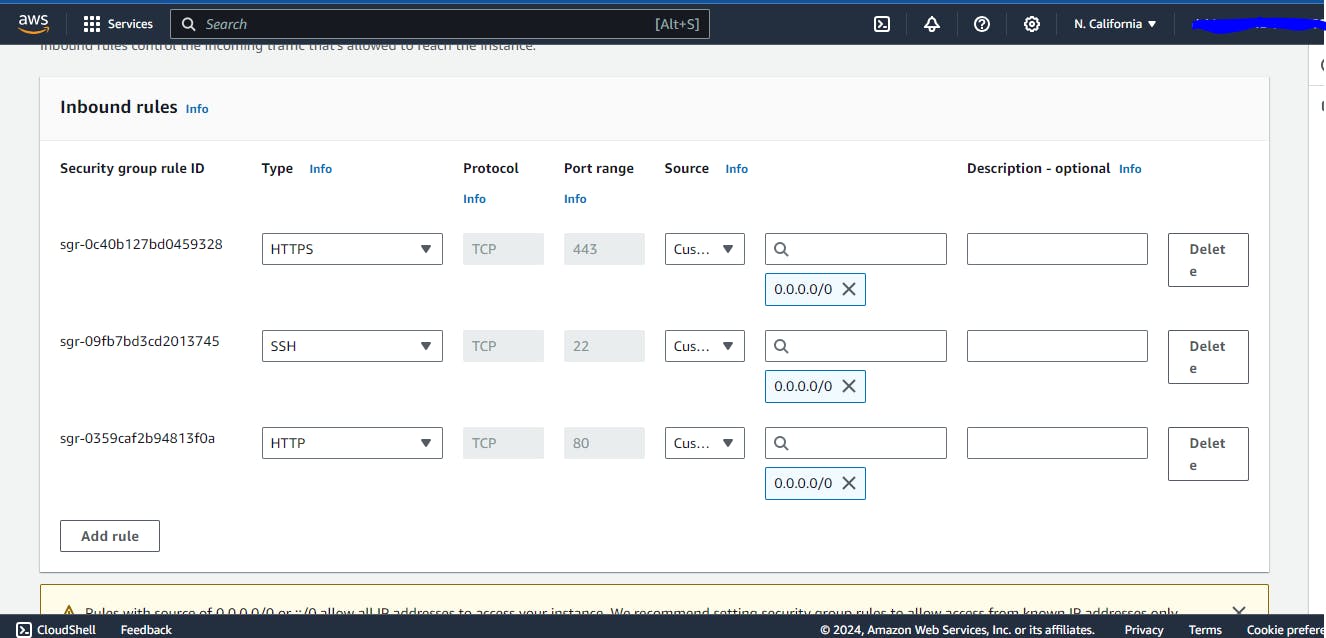
- Then connect the ec2 instance and install apache2 in each instance
sudo apt update
sudo apt install apache
sudo systemctl status apache2
sudo ufw allow 'Apache'
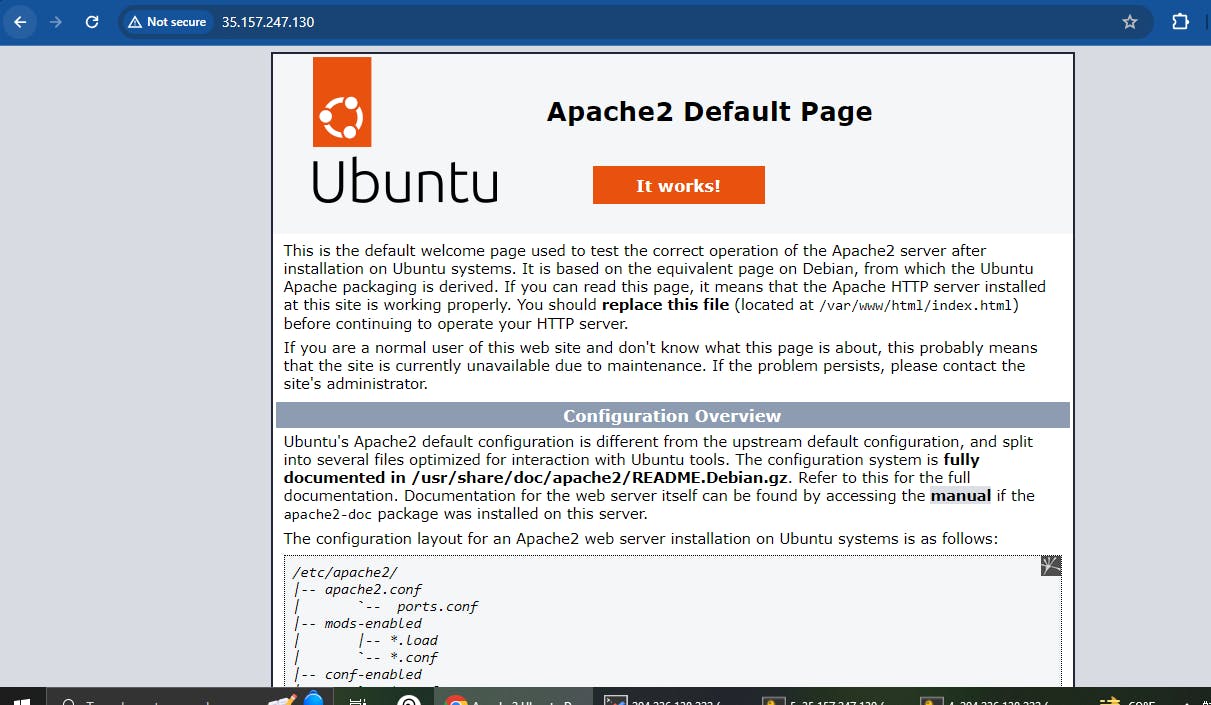
- Now, check the connection by using the curl <private ip address of peered vpc>.

Here, we are able to curl the private address of the peered vpc ec2 instance.
What if we have multiple vpc and need of vpc peering. In the above way, it makes complex and unmanaged. For this , transit gateway came to simplify the structure.
Transit Gateway simplifies network architecture by centrally connecting multiple VPCs, scaling to thousands, enabling transitive routing, and integrating with various AWS services. It offers centralized management, cross-account connectivity, and enhanced security features, making it ideal for large-scale and dynamic AWS environments.
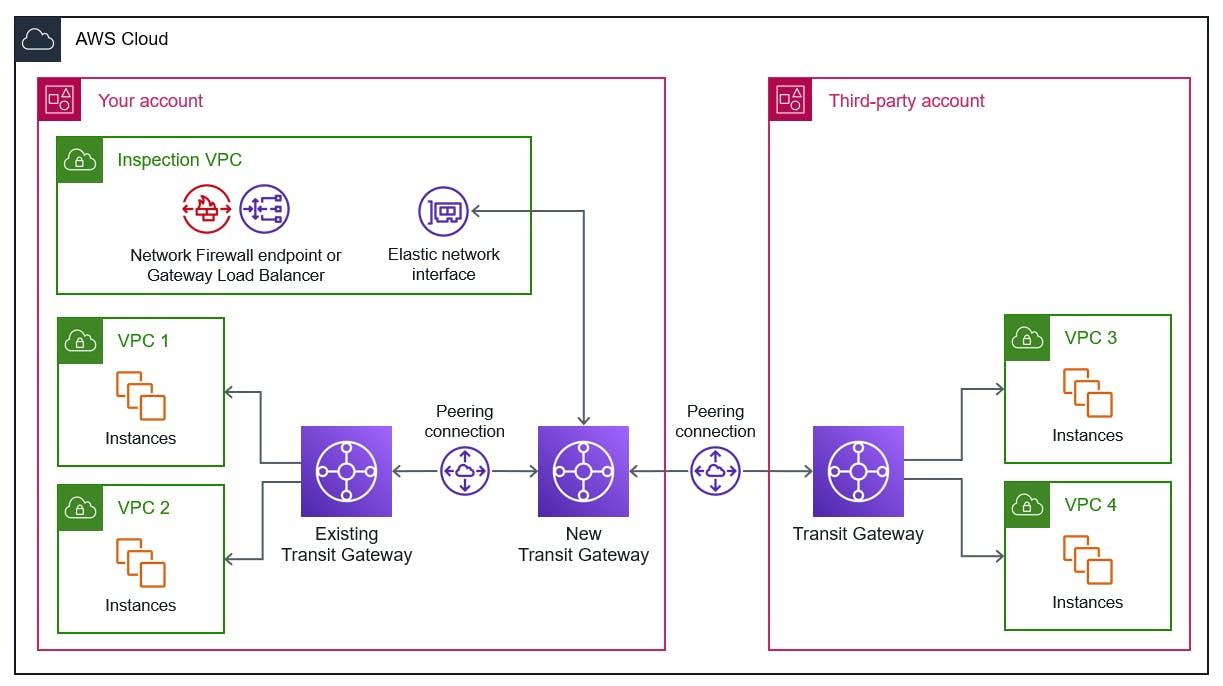
Working Mechanism
Centralized Gateway: Acts as a central hub for connecting multiple VPCs, VPNs, and on-premises networks.
Routing Tables: Uses route tables to determine the path for network traffic between connected entities.
Transitive Routing: Supports transitive routing, allowing communication between VPCs even if they are not directly peered.
Integration: Integrates with various AWS services for enhanced networking capabilities and centralized management.
Scalability: Scales to thousands of VPCs and supports cross-account connectivity for large-scale environments.
Traffic Management: Routes traffic based on defined routing rules, enabling efficient and secure communication between connected entities.
Thanks for reading.............