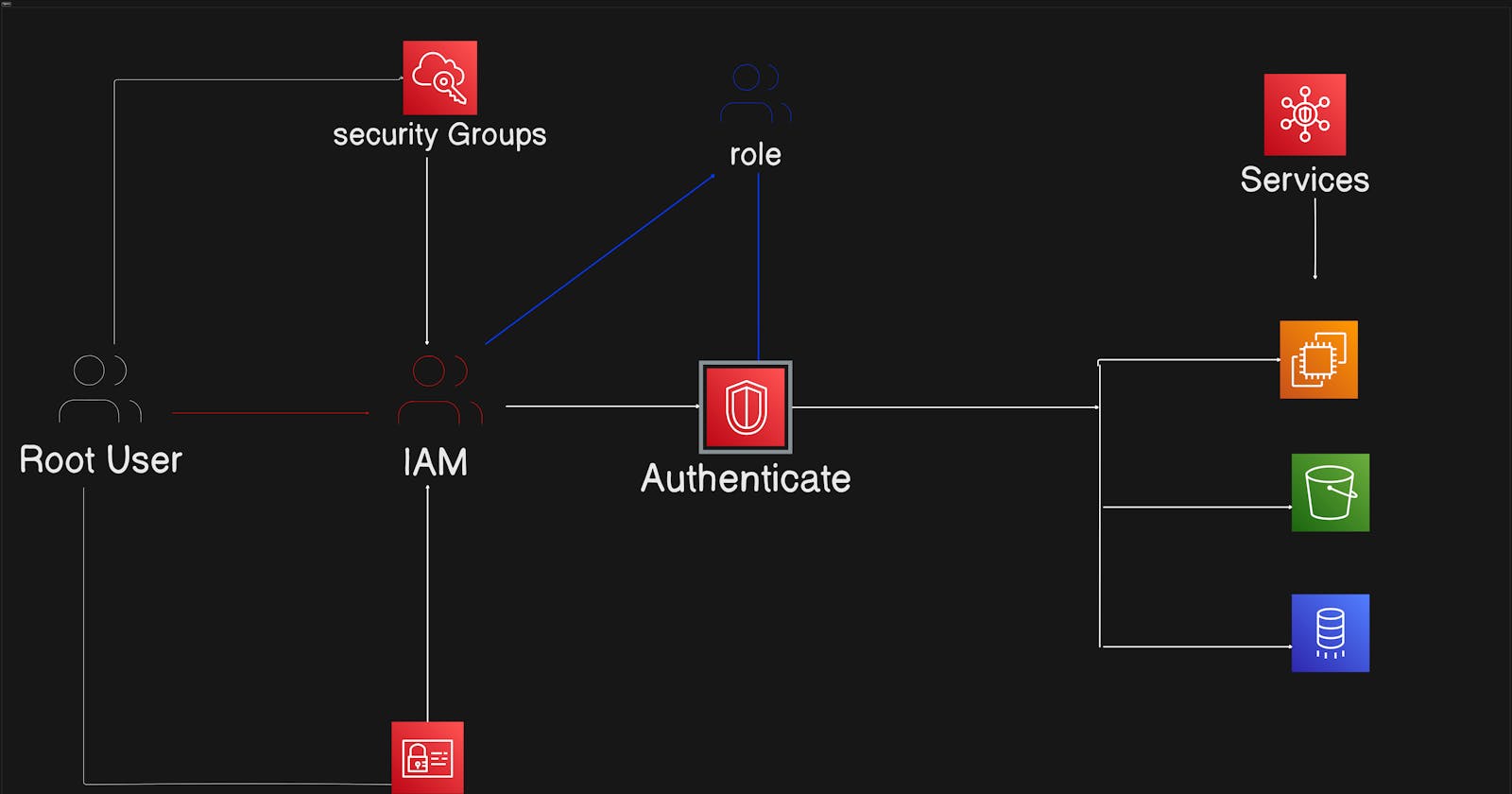
First of all, let's know the following concept
Authentication: The verification process to confirm the identity of a user or system, often involving credentials such as passwords, biometric data, or security tokens.
Authorization: The subsequent step after authentication, determining the permissions or privileges granted to an authenticated entity, dictating what resources or actions they can access within a system.
There are mainly two types of aws user.
IAM User: IAM (Identity and Access Management) user user created by root user that has its own credentials for accessing AWS services according to the policies assigned and granted permission to perform and access.
Root User: The root user is the initial account owner. This user has complete administrative access to all resources and services. It has the highest level of permissions and should be used sparingly for critical tasks like managing IAM users and billing information. It's recommended to create and use IAM users with appropriate permissions for everyday tasks rather than relying on the root user's credentials, which can pose security risks.
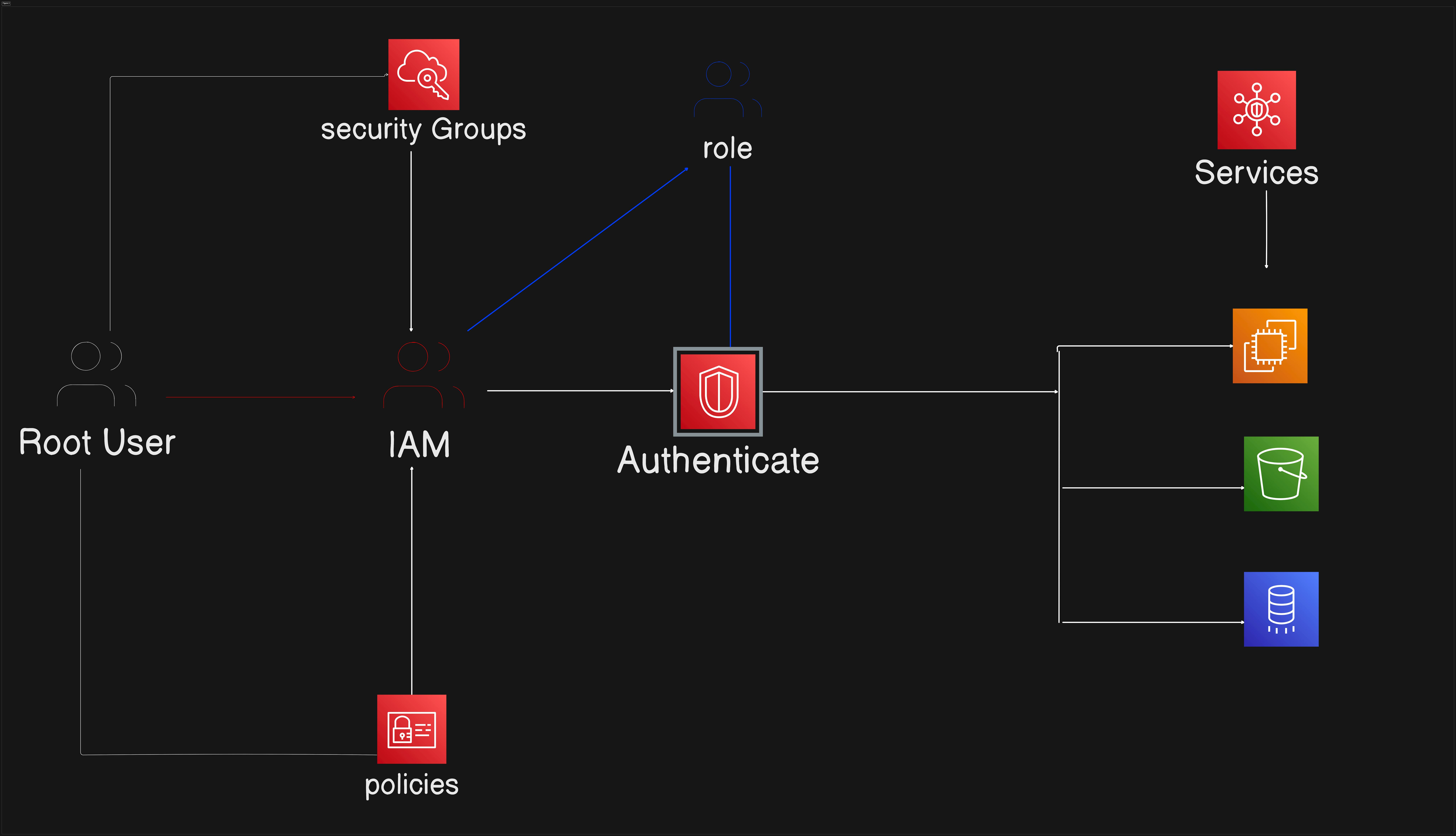
Creating an IAM User: The first step is to create an IAM user by the root (Owner) account. This user represents an individual or service that will access AWS resources. Users are created through the AWS Management Console or programmatically using the AWS CLI or SDKs.
Defining User Groups: User groups are collections of IAM users with similar access requirements. In this scenario, we'll create a group called "Developers" to group users who need access to specific AWS services or resources.
Attaching Policies to User Groups: Policies are JSON documents that define permissions and access controls. We'll create policies specifying the permissions developers need, such as accessing EC2 instances or S3 buckets. These policies will then be attached to the "Developers" group.
Assigning Users to Groups: Once the group and policies are set up, users are added to the appropriate groups based on their role or access requirements. This ensures consistency and ease of management, as permissions are managed at the group level rather than individually for each user. Also Policy can be attached directly to the user as well.
Creating Roles for Cross-Account Access: In some cases, users or services may need to access resources in other AWS accounts. IAM roles allow cross-account access without the need for sharing credentials. Roles are created with specific permissions and trust policies defining which entities can assume the role.
Steps
- Create IAM User

At first, login into your root account . Then navigate to the IAM services. And create IAM user.
Create and Assign Groups attached with policies

Unlocking Access Control: A Deep Dive into IAM Roles

IAM roles in AWS Identity and Access Management (IAM) serve as a powerful mechanism for delegating and managing access permissions within AWS environments. These roles allow entities, such as AWS services, users, or applications, to assume temporary permissions to access specific resources or perform predefined actions. This summary explores the concept of IAM roles, their benefits, and practical use cases in securing AWS environments.