First of all, Docker is a platform that enables developers to build, package, distribute, and run applications within containers. Containers are lightweight, portable, and self-sufficient units that encapsulate software and its dependencies, making it easy to deploy applications across different environments.
Docker networking refers to the networking capabilities provided by Docker, a popular platform for containerization. Containers are lightweight, portable, and self-sufficient units that encapsulate software and its dependencies, making it easy to deploy and run applications across different environments.
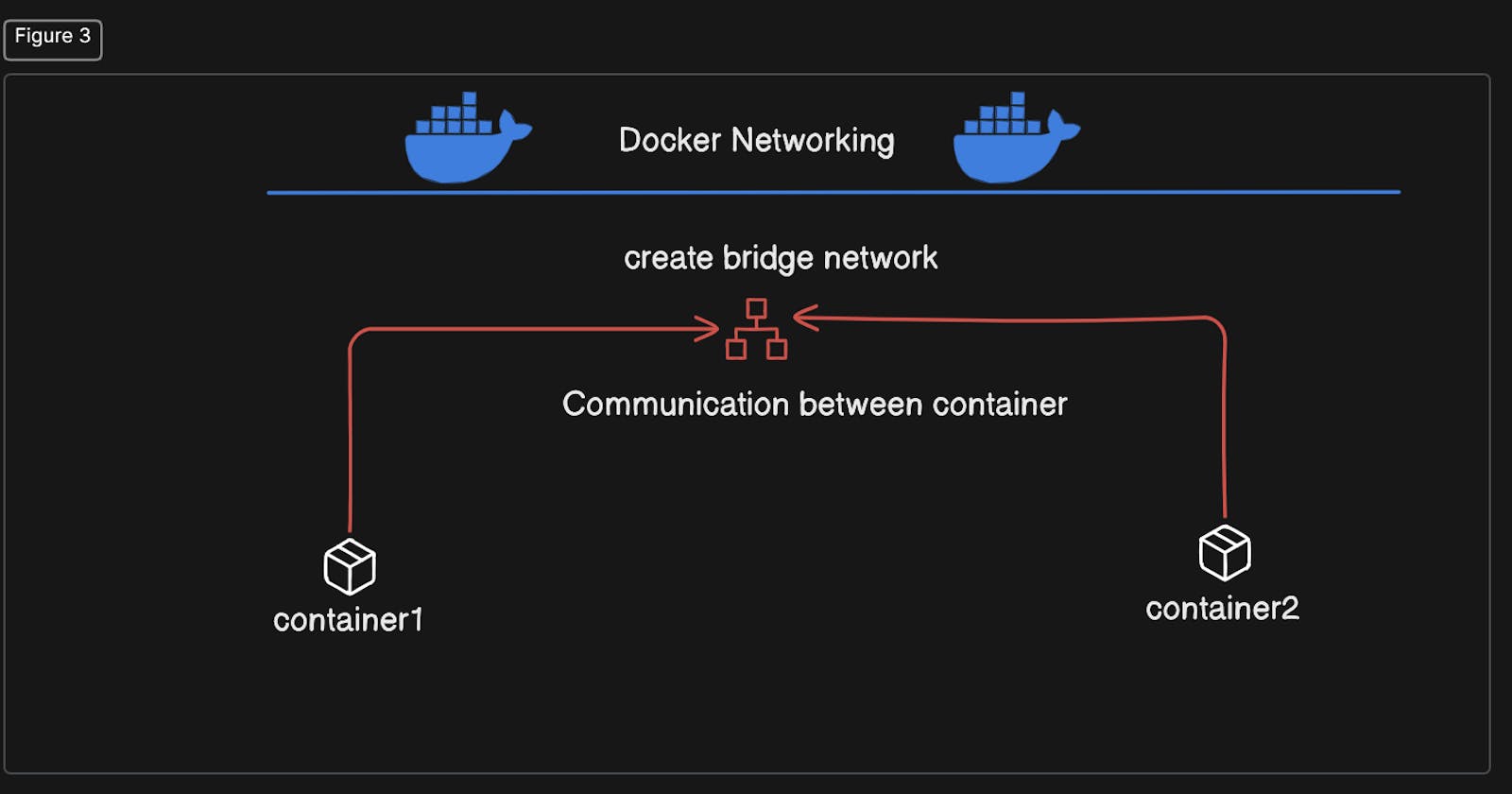
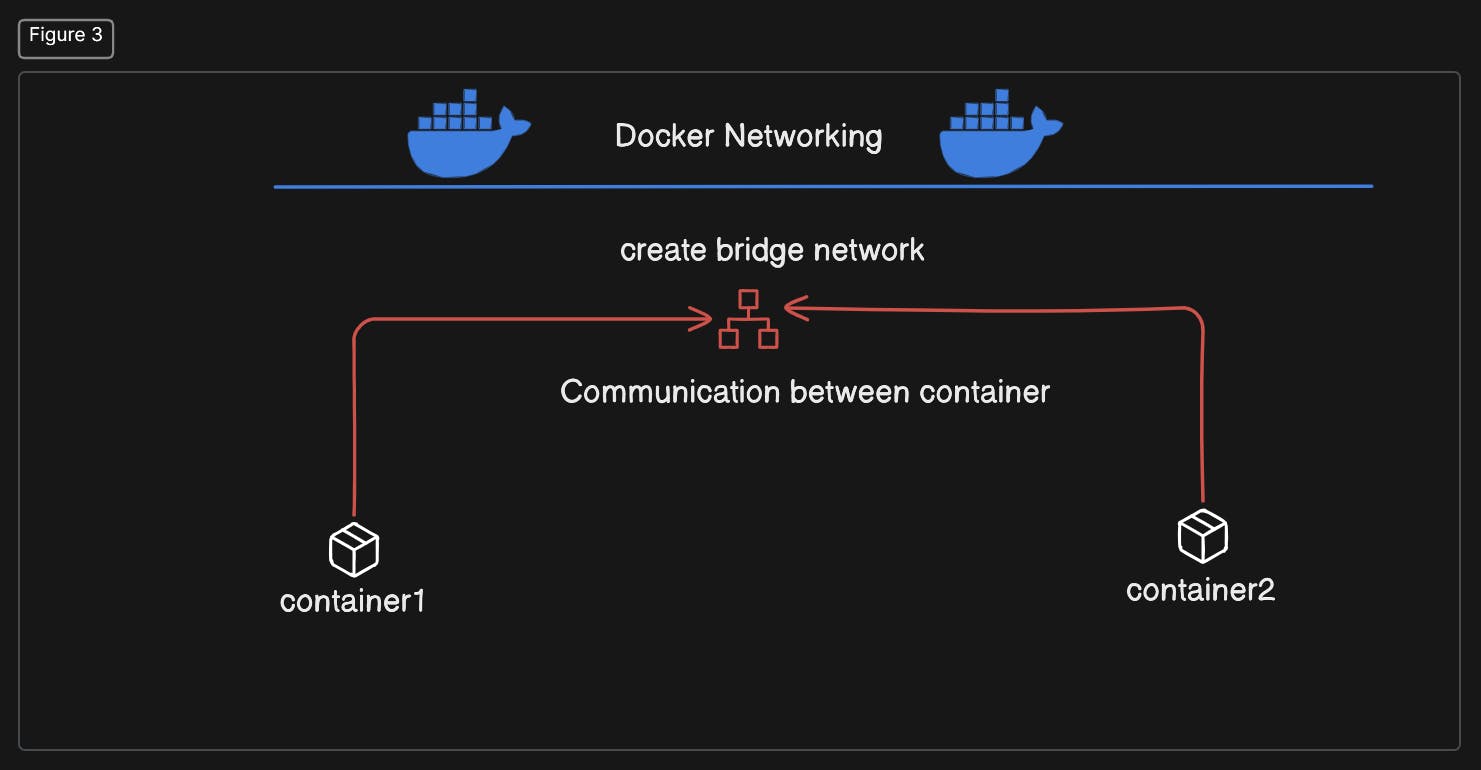
Docker networking allows containers to communicate with each other and with external networks, enabling the seamless operation of distributed applications. Docker provides several networking options, each suited for different use cases:
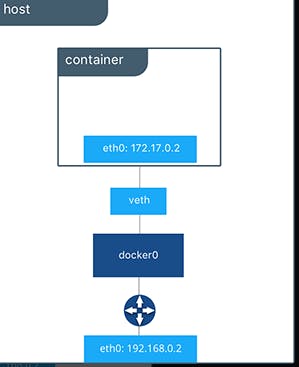
Bridge Network: This is the default networking mode for Docker. It creates a private internal network on the Docker host, and each container is assigned its own IP address within this network. Containers can communicate with each other using these IP addresses. Bridge networking also supports port mapping, allowing containers to expose specific ports to the host or external networks.
Host Network: In this mode, containers share the network namespace with the Docker host, effectively bypassing Docker's network isolation. This means that containers directly use the network interfaces of the host, which can provide better performance for network-intensive applications. However, it also exposes containers directly to the host's network, potentially reducing security and isolation.
Overlay Network: Overlay networking enables communication between containers running on different Docker hosts or across multiple Docker Swarm nodes. It creates a virtual network overlay on top of the existing network infrastructure, allowing containers to communicate securely over long distances. Overlay networks use technologies like VXLAN or IPSec to encapsulate and encrypt network traffic between nodes.
Macvlan Network: Macvlan allows Docker containers to have their own MAC addresses, making them appear as individual devices on the network. This mode is useful when you need to assign each container a unique IP address on the local network, as if they were physical machines. It provides better network isolation and allows containers to communicate directly with other devices on the network.
None Network: In this mode, Docker disables networking for containers. It can be useful for scenarios where you want to run a container without any network connectivity, such as for running batch jobs or performing local testing.
Advantages of the docker networking
Isolation: Docker networking provides isolation between containers, allowing them to run independently with their own network stack. This isolation ensures that changes or issues in one container's network configuration do not affect others.
Portability: Docker containers encapsulate applications and their dependencies, including networking configurations. This makes it easy to package, distribute, and run applications consistently across different environments, without worrying about network compatibility issues.
Flexibility: Docker offers various networking options, such as bridge, host, overlay, macvlan, and none networks. This flexibility allows users to choose the networking mode that best suits their specific use case, whether it's for local development, testing, or deploying distributed applications across multiple hosts or clusters.
Scalability: Docker networking enables the seamless scaling of applications by allowing containers to communicate with each other across hosts or nodes in a cluster. Overlay networks, for example, facilitate communication between containers running on different Docker hosts, making it easier to scale horizontally.
Performance: Depending on the networking mode chosen, Docker can offer good performance for network-intensive applications. For example, using the host network mode bypasses Docker's network isolation and allows containers to directly use the host's network interfaces, potentially improving performance for certain workloads.
Security: Docker provides built-in security features for networking, such as network segmentation using bridge networks, which helps to isolate containers from each other and from the host system. Additionally, Docker supports network policies and plugins that allow for fine-grained control over network traffic and access.
Ease of Management: Docker's networking capabilities simplify the management of networking configurations for containers. Docker Engine provides commands and APIs to create, inspect, and manage networks, making it easy to set up and configure networking for containerized applications.
Interoperability: Docker networking integrates seamlessly with other Docker features and ecosystem tools, such as Docker Swarm for orchestration, Docker Compose for defining multi-container applications, and Docker volumes for data management. This interoperability enables users to build and deploy complex, interconnected applications with ease.
Without any further delay, let's start our practical implementation. Here we will discuss about the docker bridge networking
Here,
we will create the new bridge network.
Then pull the alpine image and run the two container from that image along with name. Here the two conatiner can communicate with each other with ip because they are in the same host but cannot communicate with the container name.
Now we will create the new bridge network and connect the both container to this network and communicate with the container name. That's we want.
Make sure that you have installed Docker in your system
Steps
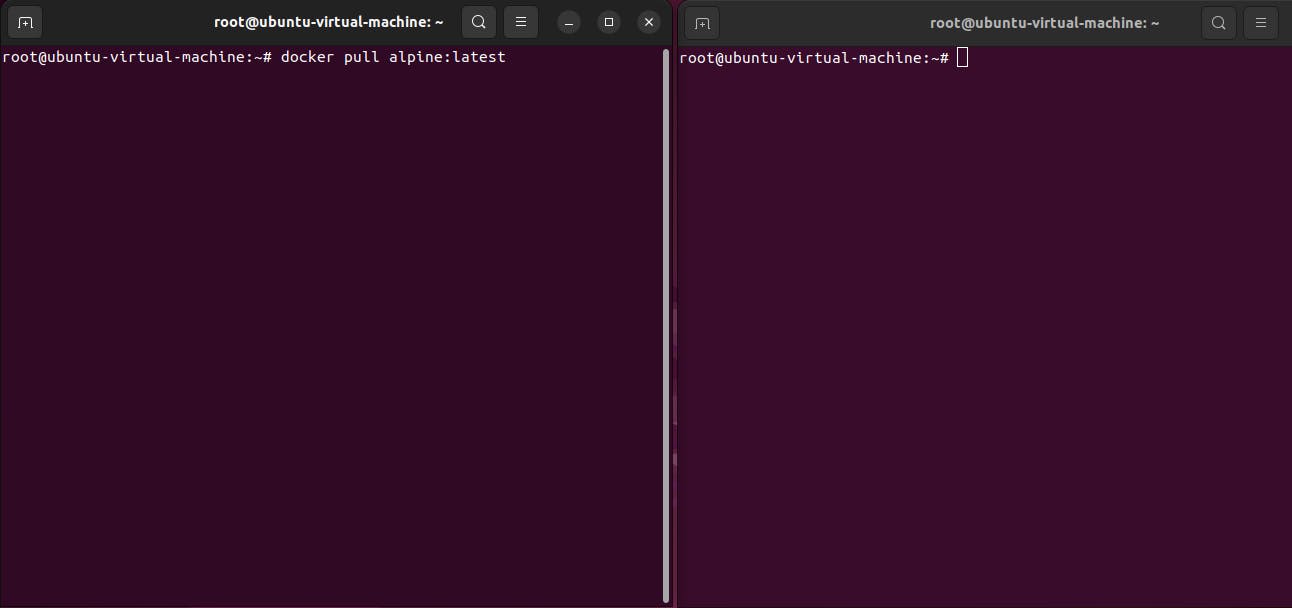
step1: Pull the latest alpine image
docker pull alpine:latest
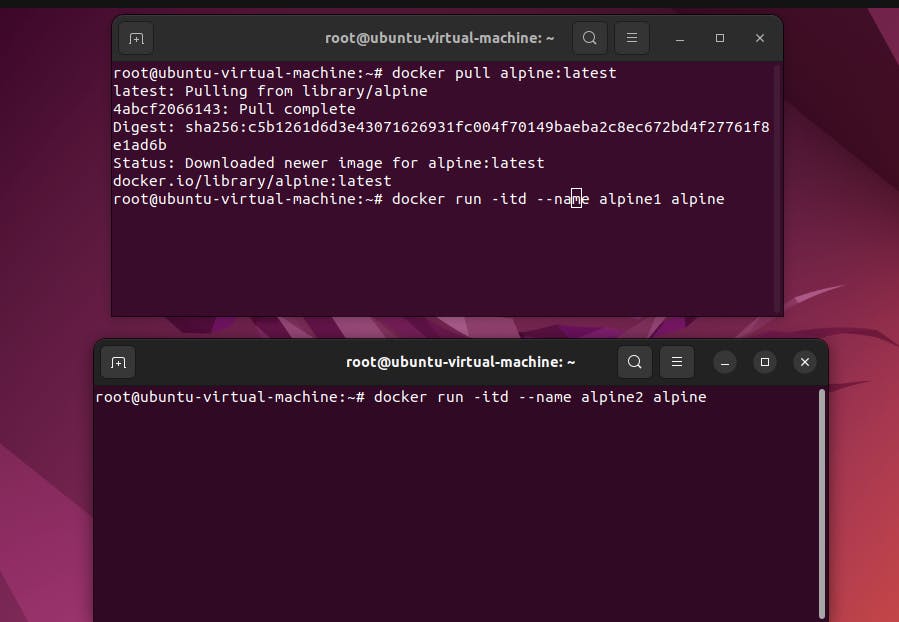
step2: Then run the container :- name alpine1 and alpine2
docker run -itd --name alpine1 alpine
docker run -itd --name alpine2 alpine
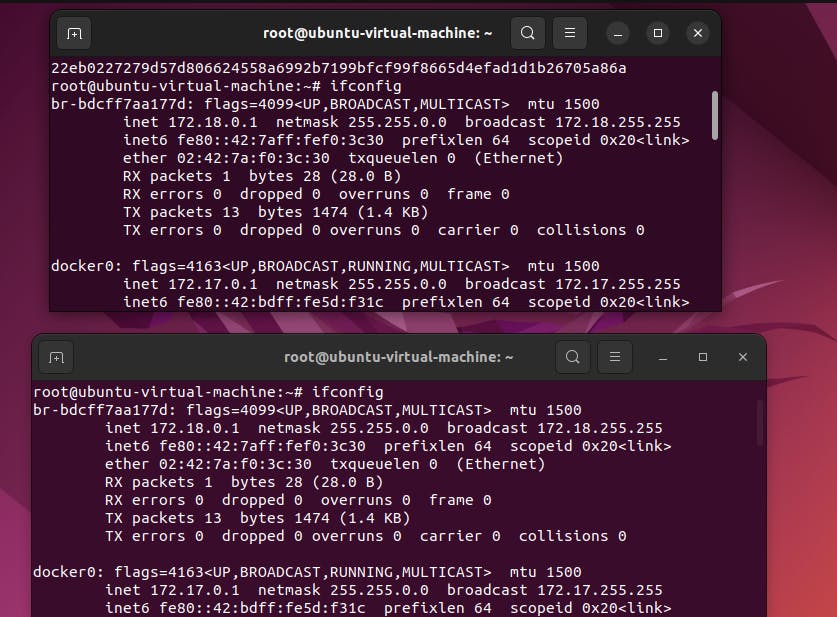
step3: Check the ip address
ifconfig
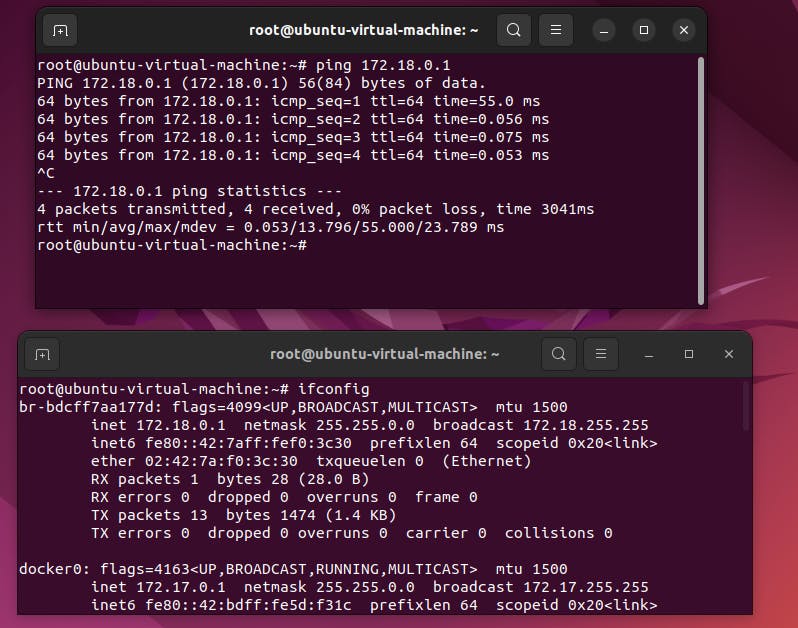
step4: Now , test to communicate with each other using host ip. You will sucess
ping <ipaddress>
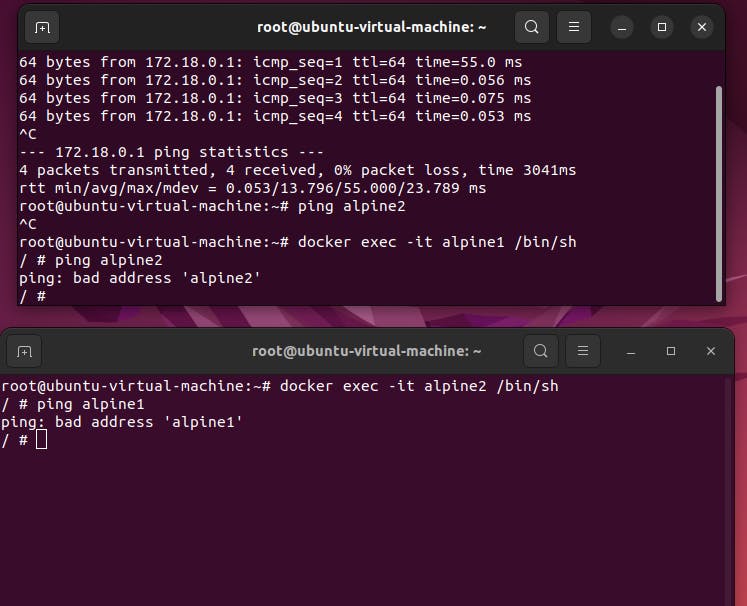
step5: Now enter into each container and ping. you will get ping failed because they are now separated from same network
#in first container
docker exec -it alpine1 /bin/sh
ping alpine2
#in second container
docker exec -it alpine2 /bin/sh
ping alpine1
step6: Now create the new Bridge network
docker network create newBridgeNetwork
docker network ls
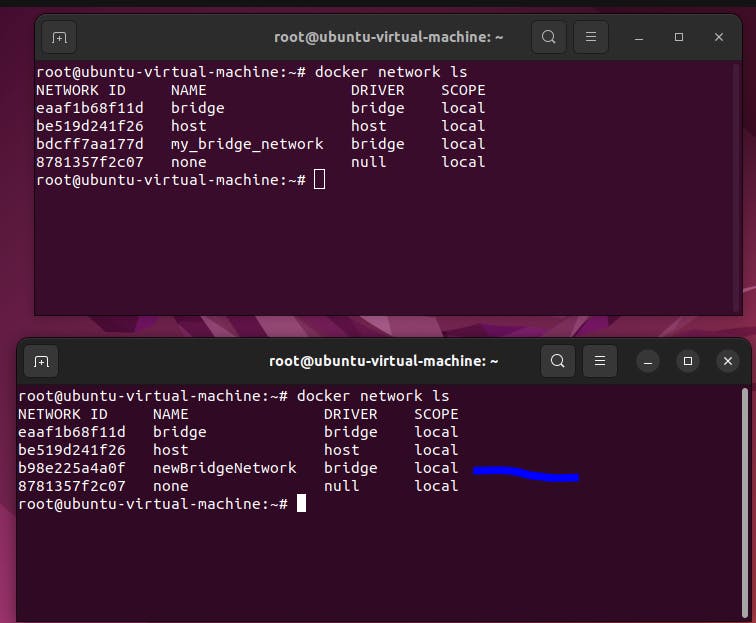
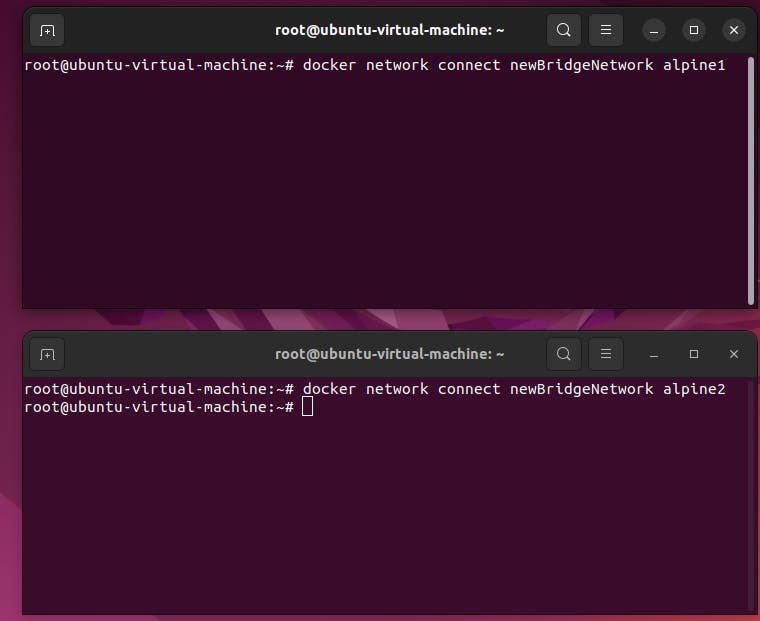
step7: Connect both container to the same newly created bridge network
docker network connect newBridgeNetwork alpine1
docker network connect newBridgeNetwork alpine2
step8: Now enter into both the container and ping each othe .
#in first container
docker exec -it alpine1 /bin/sh
ping alpine2
#in second container
docker exec -it alpine2 /bin/sh
ping alpine1
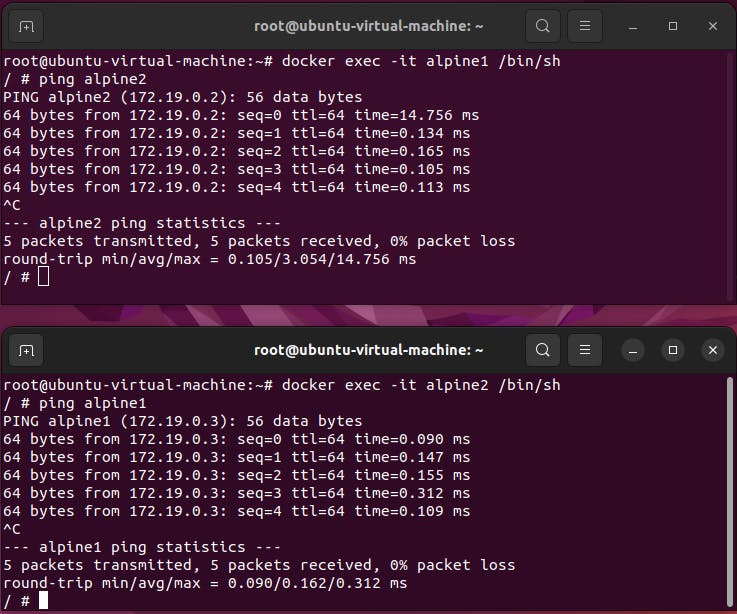
Finally, ping between the containers is sucessful.
For more :- https://docs.docker.com/engine/tutorials/networkingcontainers/
Thanks for reading.....................................