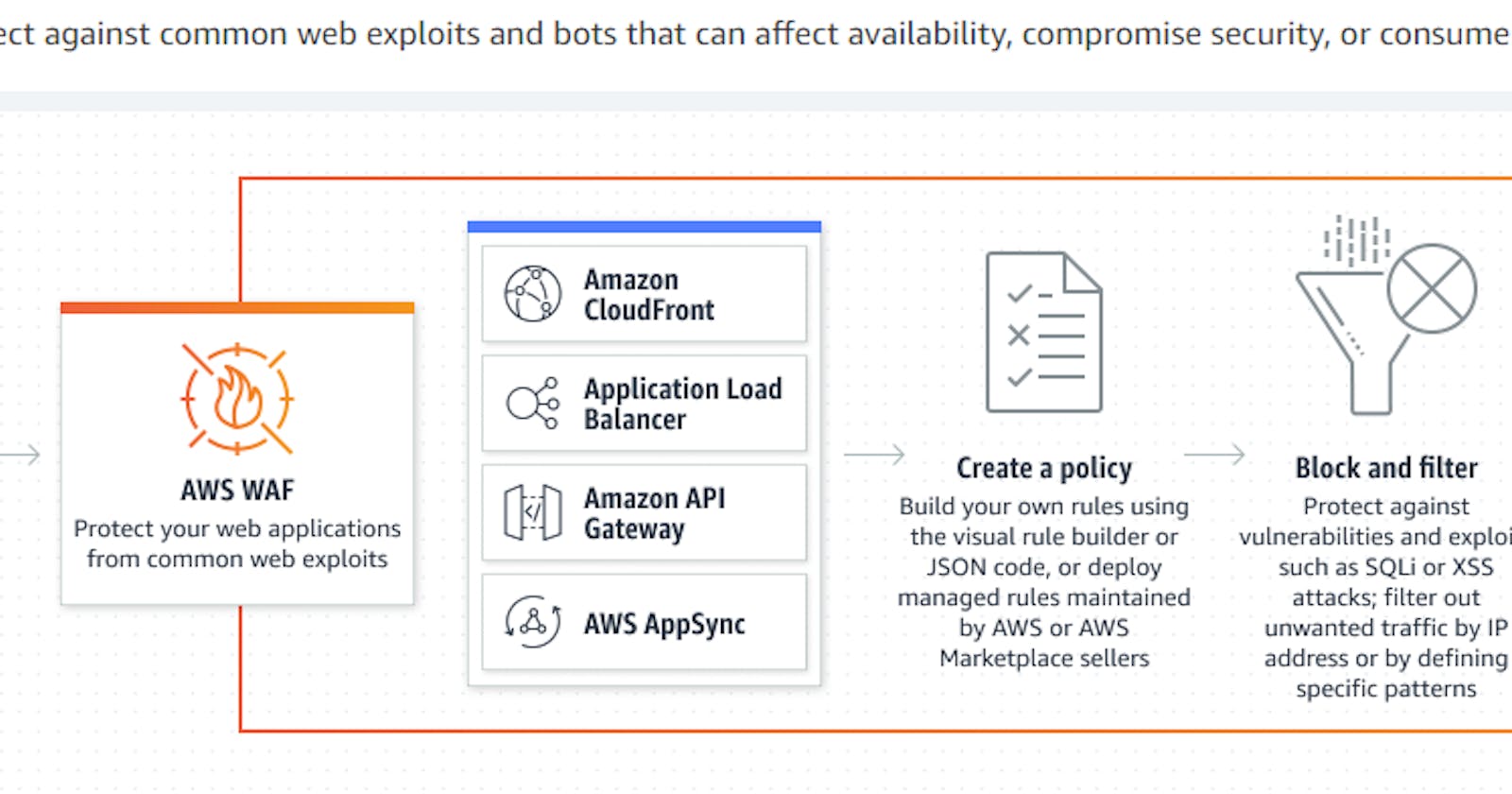
A Web Application Firewall (WAF) is a security solution designed to protect web applications from various online threats, such as SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and other types of attacks. It acts as a filter between web applications and the traffic they receive, monitoring and controlling HTTP/HTTPS traffic to and from a web application.
Benefits of WAF:
Threat Protection: WAFs help safeguard web applications against a wide range of cyber threats, including known and emerging vulnerabilities.
Data Loss Prevention: By inspecting and filtering incoming and outgoing traffic, WAFs can prevent unauthorized access to sensitive data and help prevent data breaches.
Compliance: WAFs assist in meeting regulatory requirements by providing security controls for web applications, ensuring compliance with industry standards such as PCI DSS, GDPR, and HIPAA.
DDoS Mitigation: Some WAFs offer features to mitigate Distributed Denial of Service (DDoS) attacks by filtering out malicious traffic and maintaining the availability of web applications during attacks.
Improved Performance: WAFs can help optimize web application performance by caching frequently accessed content and reducing server load through content delivery network (CDN) integration.
Working Mechanism of WAF:
Traffic Inspection: The WAF intercepts incoming and outgoing HTTP/HTTPS traffic destined for the web application.
Rule-Based Filtering: It applies predefined security rules and policies to inspect and filter the traffic based on known attack patterns, signatures, or behavioral anomalies.
Real-Time Monitoring: WAFs continuously monitor web traffic and analyze request patterns to detect potential threats and anomalies.
Blocking and Alerting: When a malicious request or suspicious activity is identified, the WAF can take action by blocking the request, alerting administrators, or applying additional security measures.
Customization: Administrators can configure custom rules and policies tailored to the specific requirements of their web applications, allowing for granular control over security settings.
Regular Updates: WAF vendors frequently update their security rules and threat intelligence to stay ahead of evolving threats and ensure effective protection against new vulnerabilities.
Steps
step 1. Create the VPC (Virtual Private Cloud) and subnets


- Create the internet gateway and attach the internet gateway to the vpc


- Create the route table and attach internet gateway to the routes of the route table and associate subnets to the route table



create the ec2 instance under the sub net and vpc with enabling auto assign public ip

Install apache 2 by using the following code
sudo apt update
sudo apt install -y apache2
sudo systemctl start apache2
sudo systemctl enable apache2

- Create the target goup with ssh and http allowed in security group


step 7. Create the Network Load Balancer

Step 8. Now If you are using the IAM user then attach full access control of waf to the iam user from the root user

step 9. Create the Weg ACL but remember don't use the space for name while creating

step 10. Create the Web Application Firewall

step 11. Create the ip set which contains the list of ips so that we can allow or block them .


step 12. Then add rule using type ipset and select the ip sets

- Now choose the action and set priority rule


Here then if we try to acces the page from the blocked ip range then we cannot like this. If we allow then we can access it although we cannot

In this way, Web Application Firewall Works to provide the security........
Thanks for the reading